前提条件
k8s集群<1.19
cert-manager
ingress-nginx
阿里云域名
申请AccessKey
登录阿里云域名所在账号,开通AccessKey并记录下来
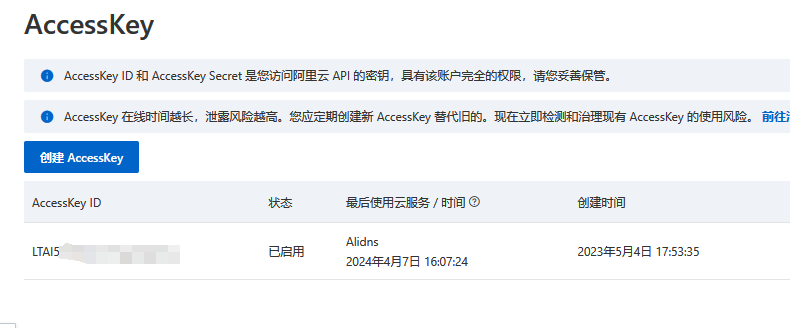
将access-key和secret-key转换成base64

将转换后的值保存为k8s secret
apiVersion: v1
kind: Secret
metadata:
name: alidns-secret
namespace: cert-manager
data:
access-key: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
secret-key: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx安装alidns-webhook
kubectl apply -f https://raw.githubusercontent.com/pragkent/alidns-webhook/master/deploy/bundle.yaml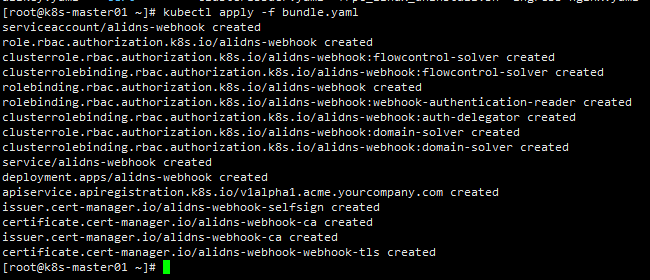
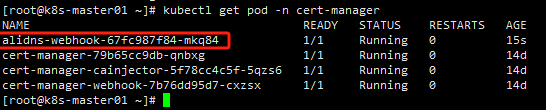
启动一个http服务
测试用,如果有服务可跳过
kind: Service
apiVersion: v1
metadata:
name: demo
spec:
selector:
app: demo
ports:
- name: http-port
port: 80
protocol: TCP
targetPort: 80
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: demo
labels:
app: demo
spec:
replicas: 1
selector:
matchLabels:
app: demo
template:
metadata:
labels:
app: demo
spec:
containers:
- name: nginx
image: nginx:1.21.6
env:
- name: TZ
value: Asia/Shanghai
ports:
- containerPort: 80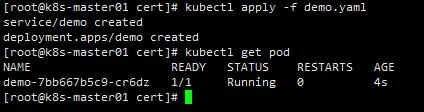
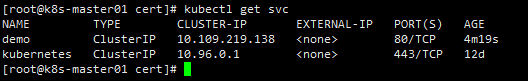
颁发机构(CA)
apiVersion: cert-manager.io/v1
kind: ClusterIssuer
metadata:
name: letsencrypt-prod
spec:
acme:
# The ACME server URL
server: https://acme-v02.api.letsencrypt.org/directory
# Email address used for ACME registration
email: user@vsoul.cn
# Name of a secret used to store the ACME account private key
privateKeySecretRef:
name: letsencrypt-prod
# Enable the HTTP-01 challenge provider
solvers:
# An empty 'selector' means that this solver matches all domains
- dns01:
webhook:
# 注意这里要改动,在https://raw.githubusercontent.com/pragkent/alidns-webhook/master/deploy/bundle.yaml中也要改动对应的groupName
groupName: acme.yourcompany.com
solverName: alidns
config:
region: ""
accessKeySecretRef:
name: alidns-secret
key: access-key
secretKeySecretRef:
name: alidns-secret
key: secret-key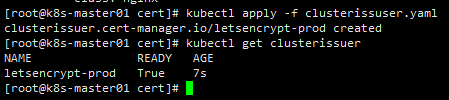
签发证书
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: demo-ingress
annotations:
nginx.ingress.kubernetes.io/force-ssl-redirect: "true" # 强制转换https
cert-manager.io/cluster-issuer: letsencrypt-prod # ClusterIssuer名称
spec:
ingressClassName: nginx
tls:
- secretName: test-tls # 证书名
hosts:
- vsoul.cn # 域名
rules:
- host: vsoul.cn # 域名
http:
paths:
- path: /
#pathType: ImplementationSpecific
pathType: Prefix
backend:
service:
name: demo # 服务名
port:
number: 80 # 服务的端口号 service port,非pod port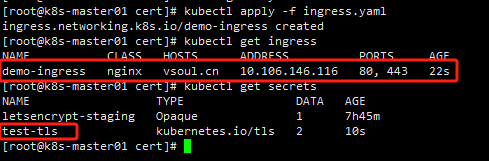
等待certificate状态为True
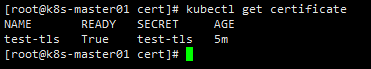
测试
浏览器通过https访问域名
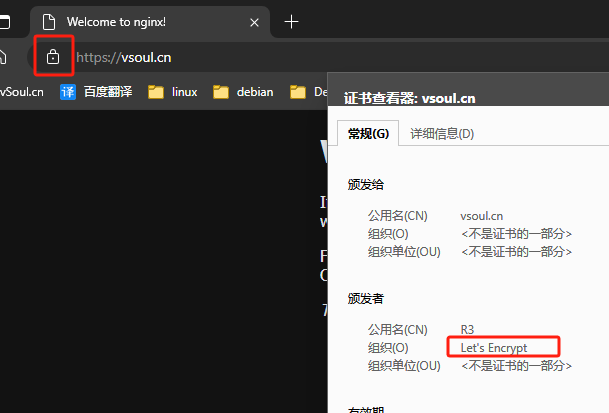
故障排查
Certificate => CertificateRequest => Order => Challenge
以此使用kubectl get、describe查看状态和日志
