自签名证书一般用于服务间或内网访问使用,在公网访问会有不安全提示。
前提条件
k8s集群<1.19
cert-manager
ingress-nginx
方式一:使用自签名作为根证书(简单明了)
创建ClusterIssuer
apiVersion: cert-manager.io/v1
kind: ClusterIssuer
metadata:
name: selfsigned
spec:
selfSigned: {}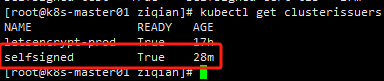
创建证书
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
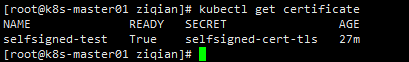
name: selfsigned-test
namespace: devops
#namespace: cert-manager
spec:
isCA: false
dnsNames: # dns列表
- sreok.cn
commonName: "*.sreok.cn"
secretName: selfsigned-cert-tls
duration: 876000h
renewBefore: 8760h
subject:
countries:
- China
localities:
- NanJing
organizations:
- sreok
organizationalUnits:
- devops
privateKey:
algorithm: ECDSA
size: 256
issuerRef:
name: selfsigned # 与clusterissusr对应
kind: ClusterIssuer
group: cert-manager.io检查证书状态,True即可使用
ingress配置
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: demo-ingress
annotations:
nginx.ingress.kubernetes.io/force-ssl-redirect: "true"
cert-manager.io/cluster-issuer: selfsigned
spec:
ingressClassName: nginx
tls:
- secretName: selfsigned-test # 证书名,与certificate一致
hosts:
- example.com # 证书域名
rules:
- host: example.com # 访问域名
http:
paths:
- path: /
#pathType: ImplementationSpecific
pathType: Prefix
backend:
service:
name: demo # 服务名
port:
number: 80 # 服务的端口号 service port,非pod port
方式二:使用CA生成链式证书(复杂、安全)
创建根证书
# 创建根证书
---
apiVersion: cert-manager.io/v1
kind: ClusterIssuer
metadata:
name: selfsigned
spec:
selfSigned: {}
---
# 创建CA
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
name: devops-ca
# 如果要根据此CA创建ClusterIssuer(集群范围)必须在cert-manager命名空间
namespace: cert-manager
spec:
isCA: true
commonName: "*.sreok.cn"
secretName: devops-selfsigned-secret
# 100年
duration: 876000h
# 1年时更新
renewBefore: 8760h
# 证书信息
subject:
countries:
- China
localities:
- NanJing
organizations:
- sreok
organizationalUnits:
- devops
privateKey:
algorithm: ECDSA
size: 256
issuerRef:
name: selfsigned
kind: ClusterIssuer
group: cert-manager.io颁发CA证书
# 基于CA创建ClusterIssuer
---
apiVersion: cert-manager.io/v1
kind: ClusterIssuer
metadata:
name: devops-issuer
spec:
ca:
secretName: devops-selfsigned-secret基于CA颁发TLS证书
---
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
name: selfsigned-tls
# ingress在哪个命名空间就写哪个
namespace: devops
spec:
# TLS证书需要禁止CA
isCA: false
usages:
- server auth
- client auth
# dns必须设置
dnsNames:
- abc.sreok.cn
# 名称需要和域名对应或包含域名
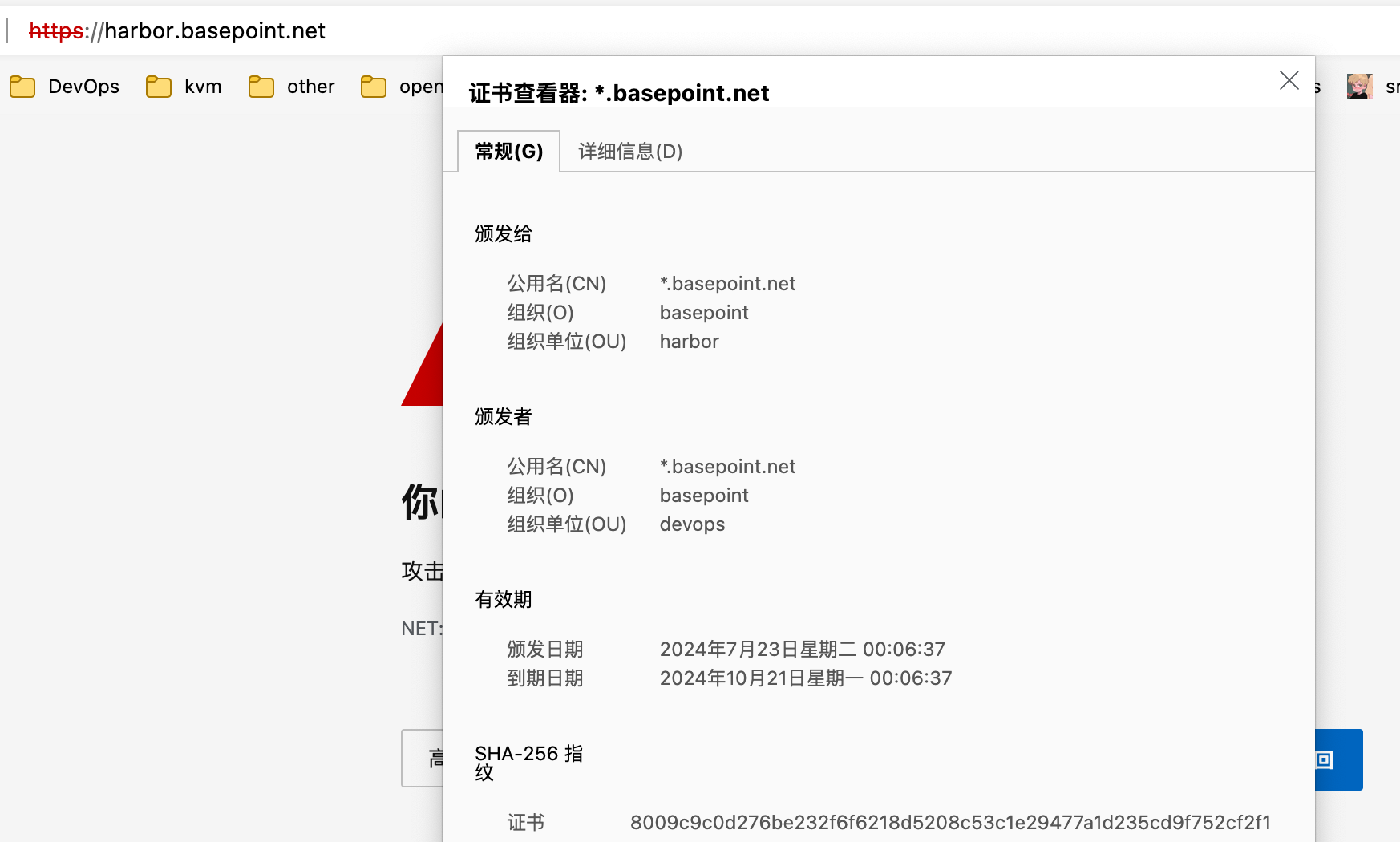
commonName: "*.sreok.cn"
# 最终TLS证书
secretName: selfsigned-cert-tls
# 100年有效期
duration: 876000h
# 有效期剩1年时更新
renewBefore: 8760h
# 证书信息
subject:
countries:
- China
localities:
- NanJing
organizations:
- sreok
organizationalUnits:
- harbor
privateKey:
algorithm: ECDSA
size: 256
# issuer绑定到CA证书
issuerRef:
name: devops-issuer
kind: ClusterIssuer
group: cert-manager.ioIngress配置
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: abc-ingress
spec:
ingressClassName: nginx
tls:
- secretName: selfsigned-cert-tls # 证书名,与certificate一致
hosts:
- abc.sreok.cn # 证书域名
rules:
- host: abc.sreok.cn # 访问域名
http:
paths:
- path: /
#pathType: ImplementationSpecific
pathType: Prefix
backend:
service:
name: demo # 服务名
port:
number: 80 # 服务的端口号 service port,非pod port测试(Harbor平台开启TLS认证)
修改hosts文件,浏览器访问域名
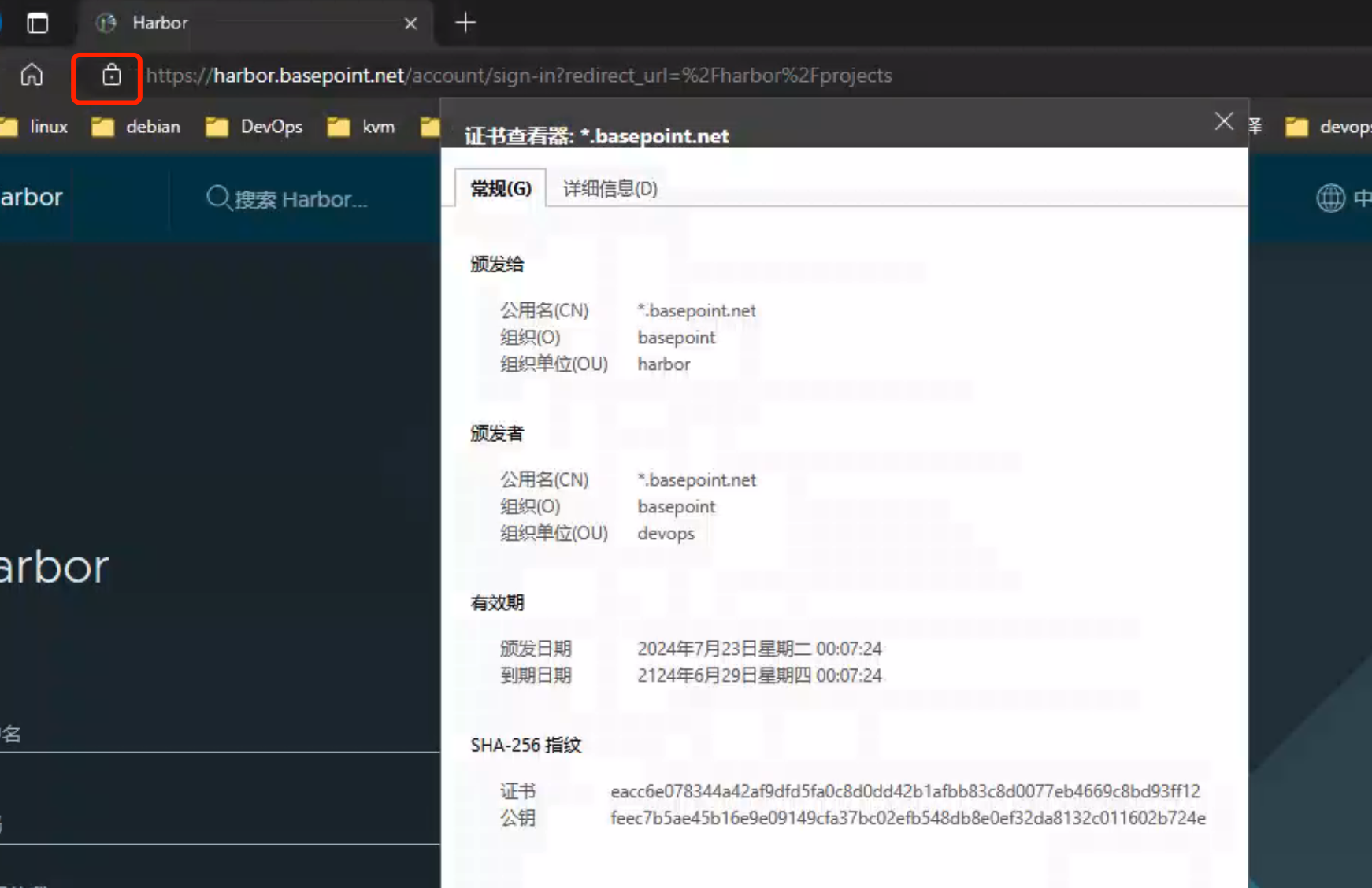
系统颁发证书
Windows
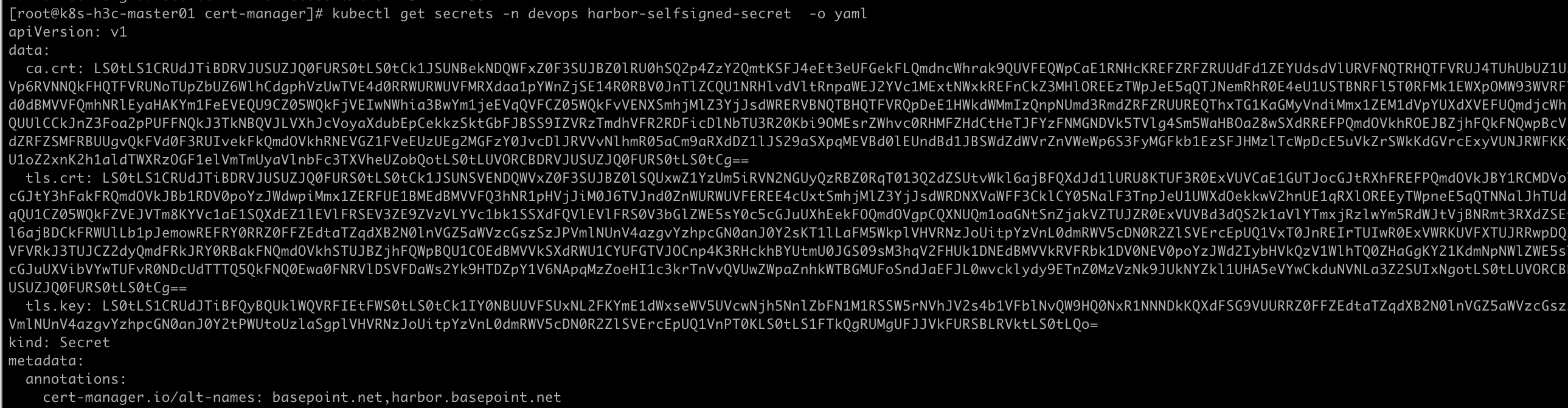
复制ca.crt内容
echo "connect in ca.crt" | base64 -d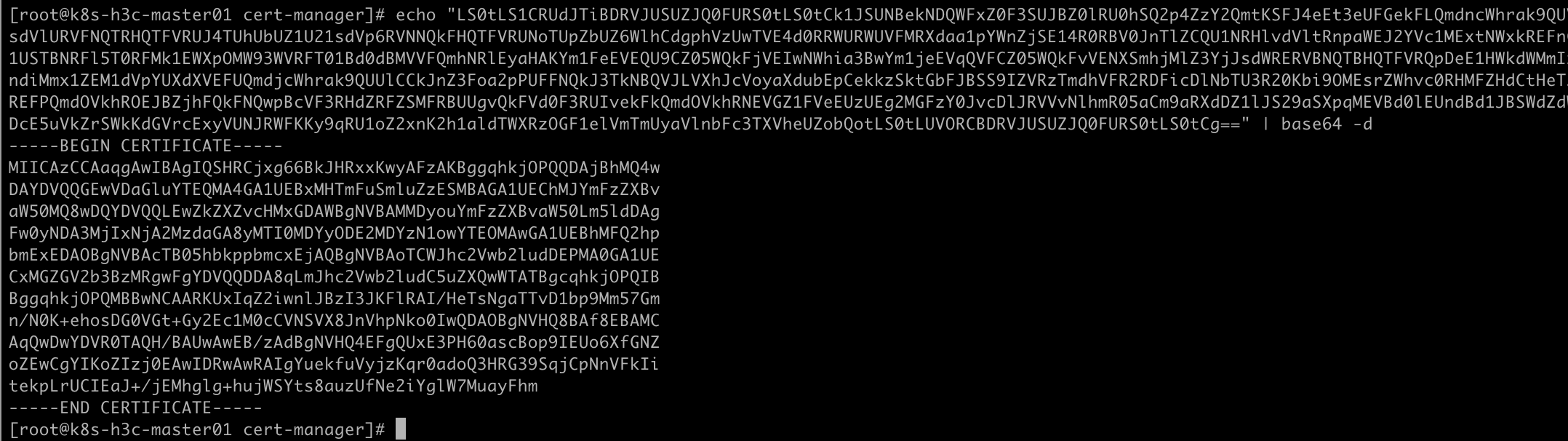
保存到电脑
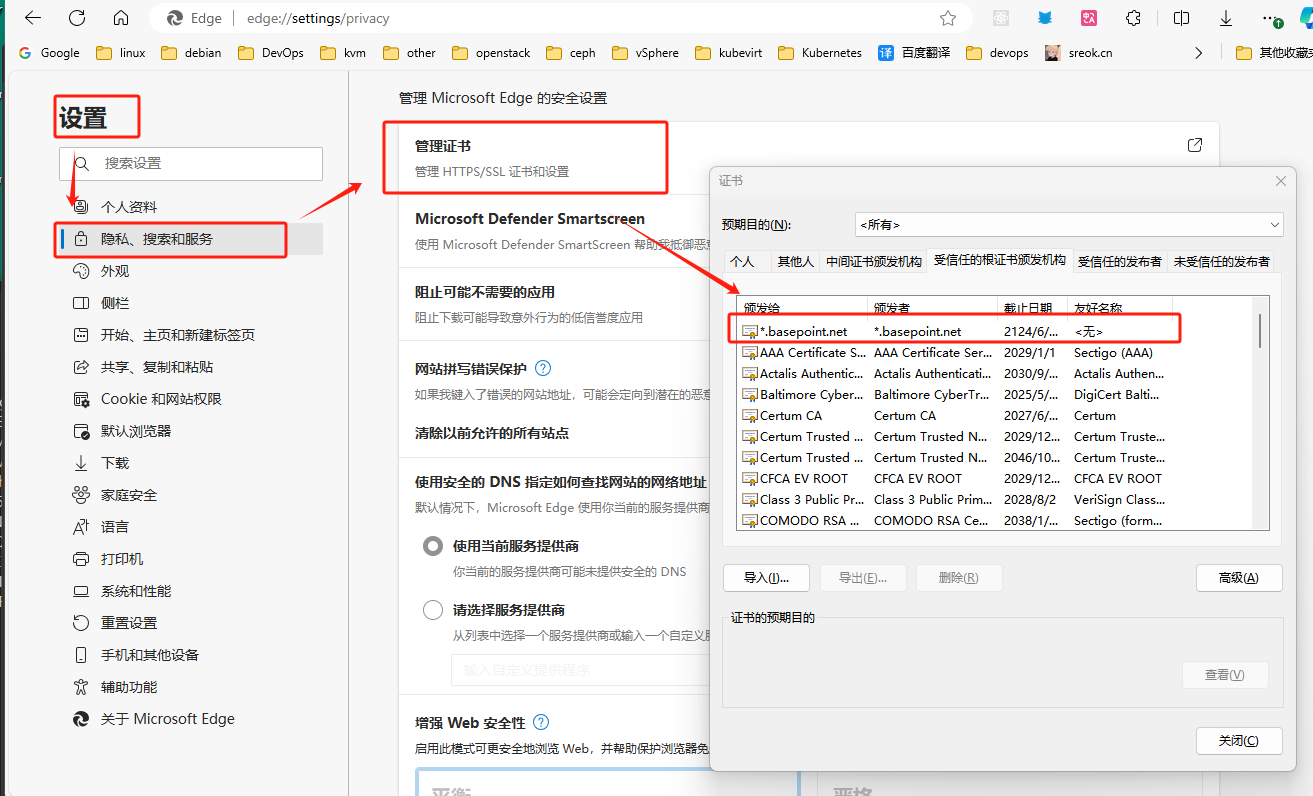
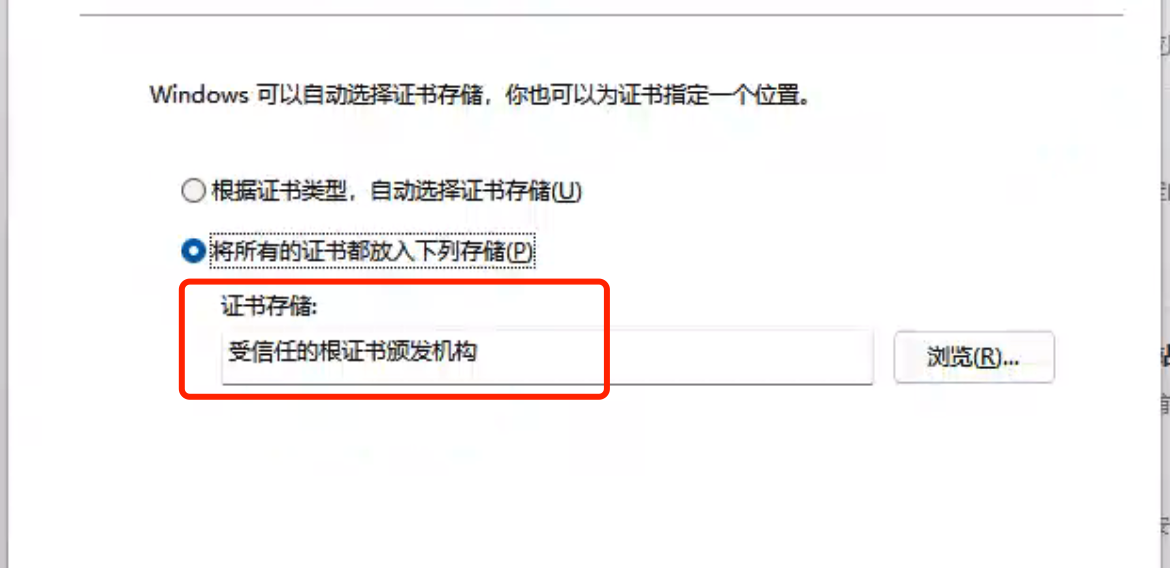
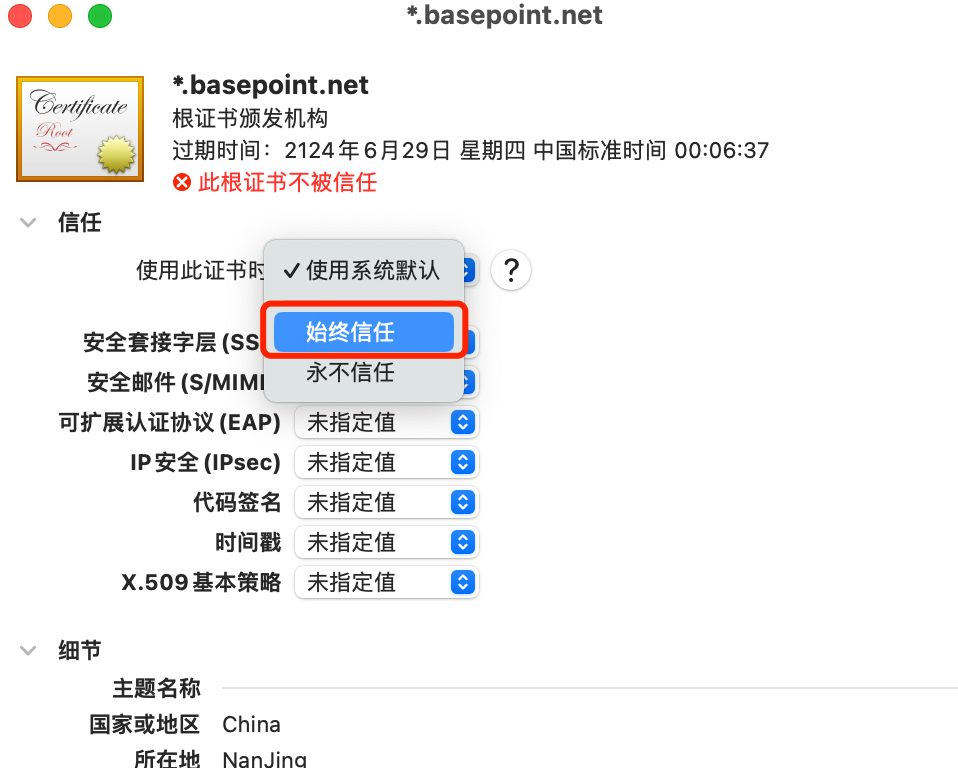
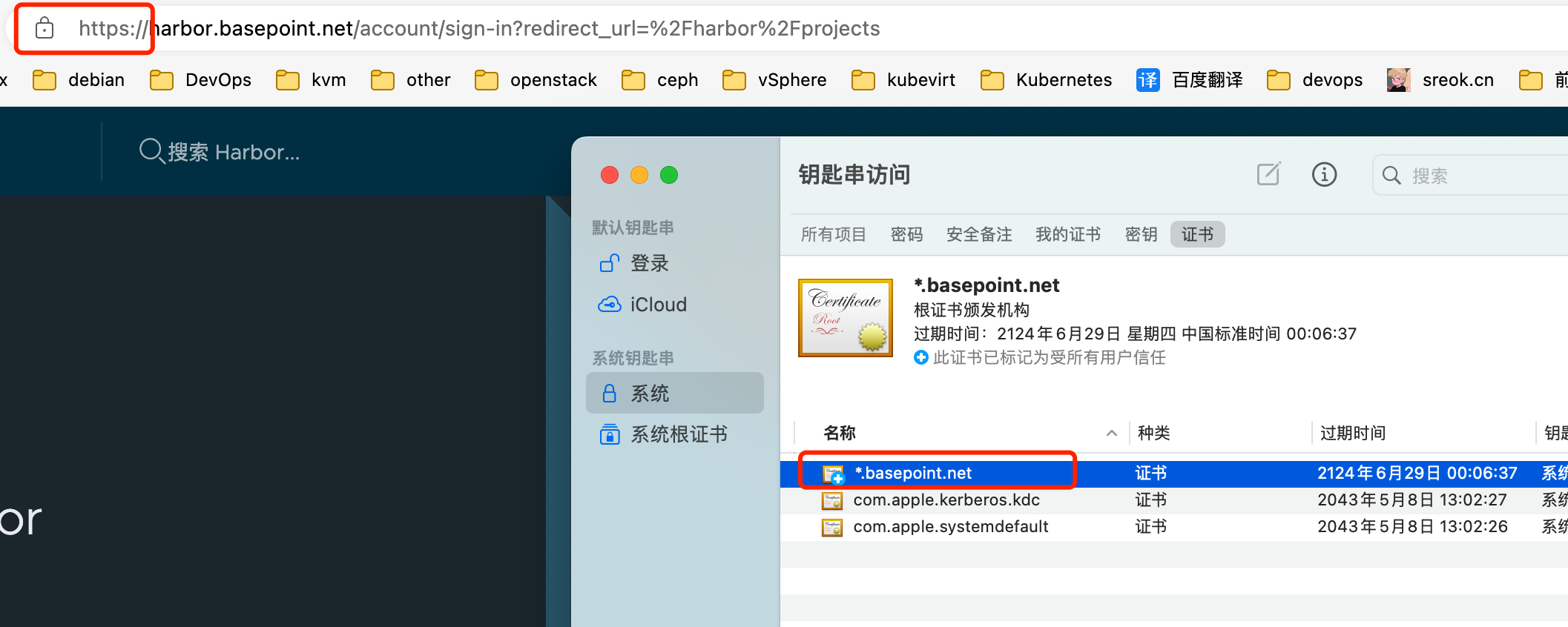
MacOS
双击导入ca.crt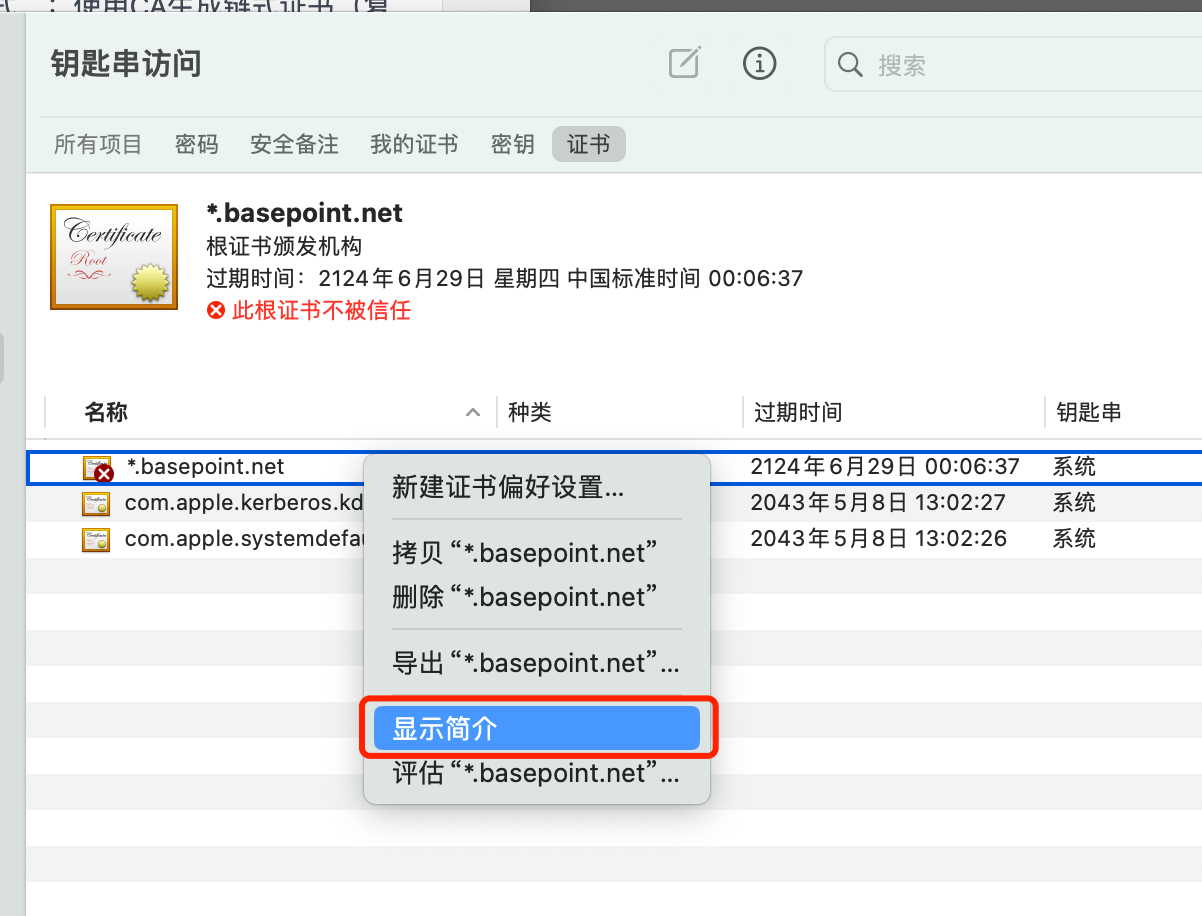
Linux
方法一:只更新TLS证书(简单)
将ca证书追加到以下文件
/etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem
方法二:全部信任此证书
安装ca-certificates,一般系统是自带的
yum install ca-certificates将证书放置以下目录
/etc/pki/ca-trust/source/anchors/执行信任此证书
update-ca-trust此操作会更新以下文件,而不是只是tls-ca-bundle.pem
/etc/pki/ca-trust/extracted/openssl/ca-bundle.trust.crt /etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem /etc/pki/ca-trust/extracted/pem/email-ca-bundle.pem /etc/pki/ca-trust/extracted/pem/objsign-ca-bundle.pem删除时在
/etc/pki/ca-trust/source/anchors/文件中删掉对应的ca证书,重新执行update-ca-trust即可。
